Increasing the Komisi Pemilihan Umum (KPU) Information Security to Protect Citizen Data
A. Introduction
Information technology has a huge impact on everyday human life. Everyone is competing to implement information technology to simplify their work while speeding up the process of completing work. Some of the benefits of using Information Technology include Information Technology can provide opportunities for people with disabilities, Information Technology can provide people with flexibility in their work, robots will take over mundane chores, and Information Technology will enable improvement in healthcare.
Because of these great benefits, the government also adopts information technology in providing services to the community. By adopting Information Technology, it is hoped that services can be reached by all communities and can be completed more quickly. One of the things that must be considered if the government will implement IT in services to the community is about the security of the system. Security is the degree of protection against criminal activity, danger, damage, and/or loss. The government must pay attention to data security from threats that may occur and threaten data security. A threat to an information resource is any danger to which a system may be exposed. The exposure of an information resources is the harm, loss or damage that can result if a threat compromises that resource. Some of the issues contained in Information Technology include privacy issues, accuracy issues, property issues, accessibility issue. Therefore, an action is needed to improve the security of information owned by the government.
B. Explanation
Several cases of citizen data stealing have occurred several times in Indonesia. For example, we take the case that recently occurred is the case of stealing of Voter Data owned by the KPU. 204 million voter data was sold by an anonymous account named Jimbo on the BreachForum site, a site used by hackers to sell their stolen data. This data contains information on full name, National Identity Number (NIK), Family Card Number, KTP Number (containing passport numbers for voters abroad), gender, date of birth, marital status, full address, and polling station code. The Communication and Information System Security Research (CISSReC) Cyber Security Institute has verified the data owned by hackers and the results match the voter data on the KPU website. The data that was successfully stolen is very dangerous because it can be misused for criminal acts by irresponsible people and can reduce public trust in government institutions. What is even more sad is that the data stealing case did not occur once but has occurred several times, namely in 2020 and 2022.
Some of the causes of the breach of Indonesian population data on the KPU website are weak in data security. KPU’s software and data security infrastructure can still be penetrated by hackers so that hackers can enter the KPU’s database and take Indonesian citizen data and then sell it online. Hackers can take advantage of the security loopholes of the website and then break into the KPU website. Another cause could be a human error committed by KPU employees by not properly maintaining access to the data they have. Hackers can take the identity of KPU employees and then use it to enter the KPU website. To obtain the data of the KPU employee, the intruder can do social engineering or create a phishing email, so that the KPU employee does not realize the data has been stolen by hackers.
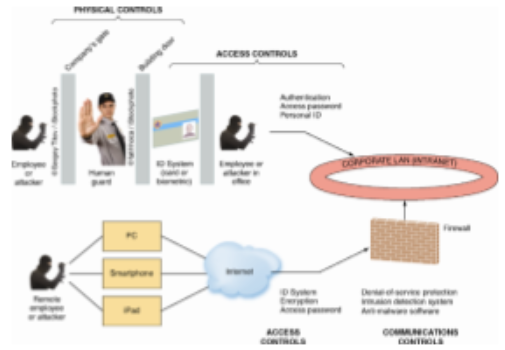
To solve several problem related to stealing data from KPU website, the first solution that can be applied is KPU should do risk management to identify the probable threats, control the threats so don’t impact the database, and minimize the impact of threat. Risk analysis must be done periodically so KPU can update the systems to identify the new threat. KPU also should do risk mitigation to prevent the risk that may be occur. Because KPU have citizen data, KPU must not tolerate any threat that may be attack to the database systems. The second solution is KPU should implement access control to their database that include physical control, access control, and communication (network) control. Physical control means that all Information Technology infrastructure such as computer and the server must be protected. Access control means anyone that don’t have authorization to access the database cannot access the database. To prevent unauthorize user, KPU must implement authentication before anyone can access the database. The authentication can be a biometric and password to prove the identity of user. communication (network) control means that movement of data across the network must be protected. This include border security control, authentication, and authorization. Furthermore, the database must be encrypted so only the receiver can access the database. If the hacker get the database, its impossible for them to open the database if the database is encrypted.
Source : Introduction to Information Systems, 9th Edition. John Willey & Sons, Inc
Furthermore, the employee of KPU should be trained about the Information Security. The should be educated about privacy, threat to information systems, and what we can do to
protect the information security in organization. The education must be done periodically so the employee can always be aware about the treat that can attack KPU database anytime. The learning material about Information Security must be updated to the current situation so the employee can know about the new threat that may be attack to information systems.
C. Conclusion
In conclusion, stealing citizen data from KPU should not be happened again in the future. KPU database contain citizen data that very confidential. If someone steal the database it can be miss use by some people to do criminal offense. Then, KPU should implement risk management so they can prevent any attack to their database. Any risk must be assessed well and carefully so they can mitigate the risk. If KPU can found any possible risk and update the new risk, they can decrease the probability of stealing data and may be no stealing data again in the future. KPU also should implement access control to their database. It also can prevent their data from the theft. The data access must be secured well so only the authorized user can access to the database. Do not forger to train the employee of KPU about Information Security so they can aware about the threat that may be affect to KPU Information Systems.
D. Reference
R. Kelly Rainer, JR, Brad Prince, (2022). Introduction to Information Systems, 9th Edition. John Willey & Sons, Inc, Chapter 3
R. Kelly Rainer, JR, Brad Prince, (2022). Introduction to Information Systems, 9th Edition. John Willey & Sons, Inc, Chapter 4 Raka Ibrahim, (2021). https://www.thejakartapost.com/life/2021/09/07/indonesians-data-just-sitting-there-hackers-say.html BBC Indonesia, (2023).
https://www.bbc.com/indonesia/articles/cgxpk9k3ye5o


