Ethics and Information Security
Ethics (also moral philosophy) is the branch of philosophy that involves systematizing, defending, and recommending concepts of right and wrong conduct. Ethic can be our guidelines to act whether in our daily activities at home, office, and also doing business. There three major areas of study within ethics: Meta-ethics, concerning the theoretical meaning and reference of moral propositions, and how their truth values (if any) can be determined, Normative ethics, concerning the practical means of determining a moral course of action, and Applied ethics, concerning what a person is obligated to do in a specific situation or a particular domain of action. Ethics also related with information ethics, which is Govern the ethical and moral issues arising from the development and use of information technologies, as well as the creation, collection, duplication, distribution, and processing of information itself (Baltzan, 2014). When we learn about Information Systems, we always concern in Information Ethics to run or analyze our business, because we can determine which one is good for our business and which one is not good for our business. In Information ethics, we can divide 4 quadrants as follows :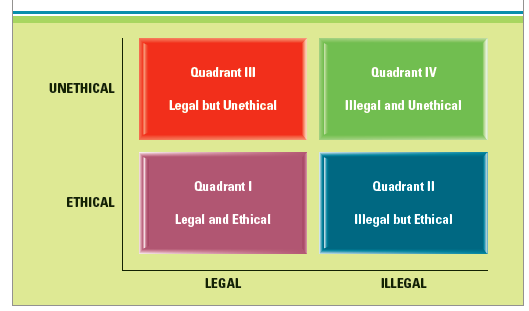 Source : (Baltzan, 2014)
Source : (Baltzan, 2014)
Based on above quadrants, we can identify our action during our working day whether is ethical, unethical, legal, or illegal. For legal but unethical is when we put email monitoring for all employees in the company for good reasons. For Illegal but Ethical is when we run business without pay the tax. In this case, information ethic is important for our daily life in business because can always remind us how to act in a good way. Ethic also related with Information Security because we need to manage company private information, such as customer data, sales data, reporting, etc. We also need to protect company’s intellectual assets from computer crime with content filtering, firewall, encryption, and antivirus software. If prevention and resistance strategies fail and there is a security breach, an organization can use detection and response technologies to mitigate the damage, such as Intrusion Detection Software. From employees themselves, commonly there are several rules regarding ethic implementation in every company that can punish the employees if they act in illegal or unethical way. So please act in a good way to protect yourself and also the company. (Marisa Karsen)


