Web Penetration Tester Software
Information Technology Security Systems, Web Servers, and Web Applications are integral parts that cannot be separated from one another. If Information Security or abbreviated as InfoSec (http://en.wikipedia.org/wiki/Information_security) is security information that is applied to a technology, where it is intended to defend information from various misuses, such as disclosure, destruction, modification, or changes in original data, for evaluation and maintaining access to assets from unauthorized parties, while Wen Server and Web Application (http://www.acunetix.com/websitesecurity/web-applications/) is a software used to communicate, send or displaying data, from or to a database server via the internet with a website search software. Usually, these applications use HTTP (HyperText Transfer Protocol).
The three things mentioned above are always connected. This is done to make it easier for users and service providers to interact with each other and carry out their daily operational activities. Apart from that, this will always grow and develop along with the increasing level of public demand for information technology services needed in the future. This is done to make the time needed for interaction to be shorter, faster, and right on the target and desired target. On the other hand, if this is done and maintained properly, it will automatically add to the image or public perception of the service provider company in the future.
But in practice, there are lots of threats or risks that arise in the interactions that are carried out, which need to be known, both by the service provider and the user himself. Among them are phishing, deface, carding, web cracking, etc. (Harkins, Malcolm, 2013). Because of the above, it is very important for technology activists, especially IT security specialists to always carry out security tests on an information technology service provided by the company to the public so that the fulfillment of security requirements can be realized and avoid various damages or service failures that have been provided. given at a later date (Walther, Ben and Hope, Paco, 2009).
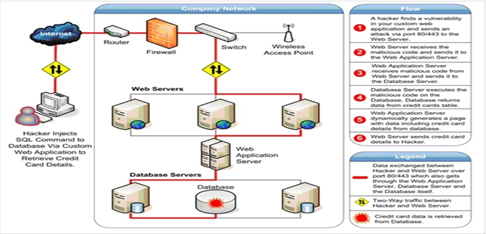
Figure 1. Web Application Attack @acunetix.com)
Figure 1 it is explained where the position of the service is usually installed and how a “cracker” carries out an attack on information owned by the company. It is hoped that with the knowledge and processes that occur, technology users will know how high the level of security is required so that the company’s awareness of the security of the services provided can be maintained against various negative things in the future. It should be noted that until now and in the future, system, and technology security attacks always lead to services based on web and mobile applications.
Because of the above, it is always necessary and tested on various information technologies that are owned. One of the tools used for testing web applications and web servers is the Acunetix application.
Sources : (http://www.acunetix.com/websitesecurity/web-applications/)

