Ethics, Privacy and Security
Nowadays, the development of technology is not only positive, but also negative. The emergence of various digital crimes known as cybercrime is the most dangerous crime in our world. Because of this problem, many countries are adopting policies that guarantee ethics, privacy, and security to solve today’s contemporary problems.
Ethics are very important to our lives. Ethics is a moral principle by which people judge what is wrong and what is right. Ethics also has a principle, but laws are often based on ethical principles, even if there are some laws that are less ethical and instead result from pushing and pulling lobbying efforts and other political pressures. Laws that are not related to ethics when an action is legal does not mean that it is ethical, for example when it is legal but not ethical and can have bad consequences.
Privacy is a special concern and protection data for every individual. There are also people who have anonymized data. Anonymity refers to someone whose identity is unknown. The positive impact of anonymity protects people who participate in online support groups where they disclose embarrassing or stigmatizing facts without fear of disclosure. However, it can also protect criminals and spammers, as well as vengeful posters that do significant damage or retaliation. But since the development of technology, there is a surveillance technology, which has the function of monitoring email, surfing the Internet and other online communication.
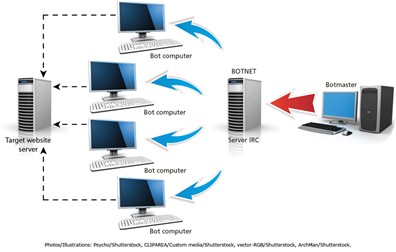
Some threats are very dangerous, such as computer viruses, malware, keyloggers, worms and Trojan horses. Distributed Denial of Service (DDoS) attack. Under the control of the botnet, the zombies send quick page requests to the target website, shutting down the server and blocking regular customers.
How do I properly solve threats? First, we have to identify the threats. If you have a problem, you can communicate with the crisis management team. Second, contain the damage. Keep calm, limit system access and take the system offline. Third, determine the cause and keep the evidence. Fourth, restore the system by restoring it from the media and getting the organization up and running. Finally, evaluate the lessons and learn by prosecuting the offender and don’t forget to re-evaluate them.
To prevent unauthorized access, we need authentication strategies that can be used to authenticate people and determine which access rights should be granted to them. Every account or ID needs a password to log in. The powerful technical control to protect sensitive data is encryption. This process uses mathematical formulas to transform the data into an illegible form so that no one can read it unless they know the key to decrypt it. However, there is a problem with cognitive problems. To reduce the cognitive burden associated with multiple passwords, we can implement single sign-on. It is a gateway service that allows users to log on once with a single user ID and password and access multiple software applications.
References :
– https://binusmaya.binus.ac.id/newStudent/#/class/resources.ISYS6093/007404/1910/CL/20005
– http://jurnalnasional.ump.ac.id/index.php/KOSMIK/article/view/3439/2153

